Authors:
(1) ZHIYUAN WEI, Beijing Institute of Technology, China;
(2) JING SUN, University of Auckland, New Zealand);
(3) ZIJIAN ZHANG, XIANHAO ZHANG, XIAOXUAN YANG, and LIEHUANG ZHU, Beijing Institute of Technology, China;
(4) XIANHAO ZHANG, Beijing Institute of Technology, China;
(5) XIAOXUAN YANG, Beijing Institute of Technology, China;
(6) LIEHUANG ZHU, Beijing Institute of Technology, China.
Table of Links
Overview of Smart Contracts and Survey Methodology
Vulnerability in Smart Contracts
Conclusions, Acknowledgement and References
2 OVERVIEW OF SMART CONTRACTS AND SURVEY METHODOLOGY
2.1 Smart Contracts
The basic idea of smart contracts can be attributed to Nick Szabo, who introduced the concept in 1996, predating the creation of blockchain technology. Szabo envisioned smart contracts as computer protocols that enable parties to engage in digitally verifiable and self-executing agreements. These contracts are written in code format and facilitate secure and efficient transactions, reducing costs and expediting execution compared to traditional contracts [120]. However, the development of smart contracts faced challenges in trustless systems until the emergence of Ethereum in 2015 [74]. Ethereum’s introduction of a blockchain-based platform specifically designed for executing smart contracts revolutionized the field. Ethereum’s success paved the way for the proliferation of other blockchain platforms that also support smart contract development. These platforms include Hyperledger [110], EOSIO [64], Tezos [27], NEO [90], and even Bitcoin, which implemented its own version of smart contracts [26]. We present a comprehensive comparison of four prominent blockchain platforms, highlighting their similarities and differences in terms of smart contract implementation and security.
• Bitcoin primarily aims to facilitate secure peer-to-peer currency transactions without the need for intermediaries. While Bitcoin was not originally designed to support extensive smart contract functionalities such as those of Ethereum, it does provide limited capabilities for executing cryptographic protocols. Bitcoin smart contracts are primarily written in a programming language named Script, which is a simple, stack-based programming language that is specifically designed for transactions. These smart contracts on Bitcoin are often referred to as script-based contracts. Researchers have focused on studying the construction and capabilities of Bitcoin’s scripting language, such as Ivy [1], BALZAC [23], SIMPLICIT [93], and BITML [22].
• Ehtereum is the pioneering blockchain platform that introduced the deployment of smart contracts. It allows developers to create their own smart contracts using Solidity, a Turing-complete programming language. These smart contracts are executed on the Ethereum Virtual Machine (EVM), which provides a runtime environment for their execution. The introduction of smart contracts on Ethereum has significantly expanded the range of applications and use cases for blockchain technology. This development has given rise to a new paradigm known as Decentralized Applications (DApps), which leverage the capabilities of smart contracts to enable decentralized and trustless interactions. Solidity is designed specifically for Ethereum and allows developers to write code that complies with EVM bytecode, which is the low-level representation of smart contracts.
• Hyperledger Fabric (HF) is a blockchain platform designed primarily for enterprise. Unlike public blockchains like Bitcoin and Ethereum, HF operates on a permissioned network where a defined set of trusted organizations participate through a membership service provider [16]. In Hyperledger Fabric, smart contracts are referred to as chaincode. One of the notable advantages of HF is its flexibility in terms of programming language support for writing chain codes. Developers can choose from various programming languages such as Golang, Java, and JavaScript to implement their smart contracts, allowing them to leverage their existing expertise and use the most suitable language for their application [74]. Privacy is another key feature of HF smart contracts.
• EOSIO introduces several innovative features to the field of blockchain technology, e.g., delegated proof of stake consensus (DPOS) and updatable smart contracts [64]. EOSIO supports a range of programming languages, including C++, Python, and JavaScript, giving developers the flexibility to choose the language they are most comfortable with and that best suits their application requirements. This multi-language support enables developers to leverage their existing skills and expertise, making it easier to create and deploy smart contracts on the EOSIO platform. One key advantage of EOSIO smart contracts is their ability to handle high transaction throughput with almost 4,000 transactions per second (TPS) [7].
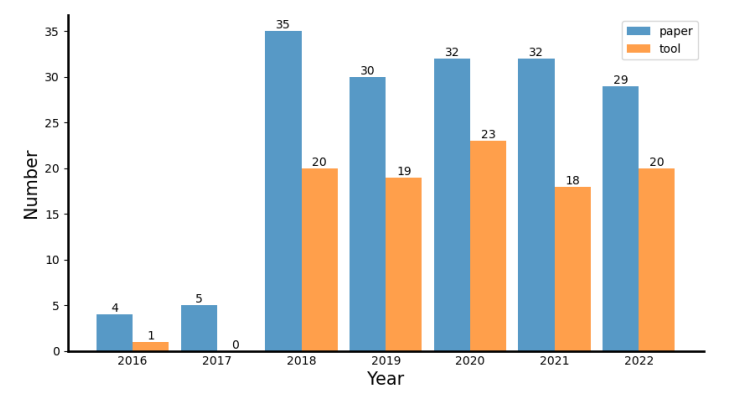
As the use of smart contracts becomes more widespread, the importance of their security cannot be overstated. In the past few years, smart contracts have suffered from an increasing number of security issues, leading to financial losses and reputational damage. Therefore, it is crucial for academics and industries to pay attention to the security of smart contracts and develop techniques and tools to ensure their safety. Figure 1 illustrates an increasing trend in both academic papers and software tools from 2016 to 2020, indicating a growing interest and activity in smart contract research and development. However, there has been a slight linear descent in the number of papers and tools in the subsequent years of 2021 and 2022, which may suggest a possible stabilization or saturation of the field. This further indicates a perfect timing for conducting a substantial literature review of the field. Nevertheless, it is important to note that the numbers alone do not provide insights into the quality or impact of the papers and tools.
2.2 Survey Methodology
The objective of our survey is to provide a comprehensive analysis of different approaches to dealing with vulnerable smart contracts. To achieve this, we have formulated a set of Research Questions (RQ) that outline the scope of our review:
RQ 1: [Vulnerabilities] What are the common vulnerabilities that exist in smart contracts, and how can we classify them based on their characteristics?
RQ 2: [Attacks] How do attackers exploit these vulnerabilities, and what are the consequences of these attacks on smart contracts?
RQ 3: [Defenses] What defense methodologies are available to protect smart contracts against attacks, and how do these defenses mitigate the risks associated with vulnerabilities?
RQ 4: [Effectiveness] How effective are the existing vulnerability analysis tools in identifying and detecting vulnerabilities in Solidity smart contracts, and what are the strengths and limitations of these tools in terms of accuracy, performance, and coverage?
RQ 5: [Tools and Benchmark] How do we select representative vulnerability analysis tools for evaluation, and how can we create a standardized benchmark of vulnerable and correct smart contract cases to evaluate the effectiveness of these tools?
By addressing these research questions, our survey aims to provide comprehensive insights into the vulnerabilities, attacks, defense mechanisms, effectiveness of analysis tools, and the creation of a benchmark for smart contracts. To achieve this, we conducted extensive searches across various databases and search engines, including Google Scholar, IEEE Xplore, ACM Digital Library, Springer Link, Scopus, and preprint repositories. We employed the following keywords and search terms: “blockchain" AND “smart contracts" AND “vulnerabilities" OR “security" OR “attacks". Next, we anticipate a substantial number of search results that require screening to identify relevant papers. The screening process generally consists of two stages: a title and abstract screening stage, followed by a full-text screening stage [101]. Once we have identified the relevant papers, we assess their quality based on predefined inclusion criteria. This generally involves assessing the relevance, methodology, validity, reliability, credibility, clarity, and impact. The selected papers should address the topic of smart contracts in a meaningful way and provide valuable insights for our investigation. The methodology employed should be suitable for addressing our research questions, transparent, and capable of being replicated. The results should be accurate and consistent, and the conclusions drawn should be well-supported by the data. The authors should present their ideas clearly and concisely, with the paper being free of errors and inconsistencies. Furthermore, the paper should have made a significant contribution to the field of smart contracts.
After evaluating these quality attributes, we have collected 174 related papers from 72 conference proceedings (including CCS, IEEE S&P, NDSS, USENIX, Euro S&P, Financial Crypto, ASIA CCS, ICSE, ASE) and 11 journals (including IEEE TSE, IEEE COMST), as well as preprints published between 2015 and 2022. Once we have assessed the quality of the selected papers, we proceed to extract the relevant data from them. This process involves gathering information about the research questions, methodology, findings, and conclusions presented in each paper. We have described the collected articles in an online repository available at: https://sites.google.com/view/weifar-sc-survey-publication.
This paper is available on arxiv under CC 4.0 license.

